Attach IAM Role to EC2 Instances
Using IAM roles with your EC2 instances has been the recommended best practice for managing AWS credentials deployed to your instances. Previously, an EC2 instance needed to have an IAM role assigned to it at launch time. Only recently has AWS allowed IAM roles to be associated with EC2 instances after the EC2 instance has been launched.
Today, we’re happy to announce a new action in our ever-growing list of action types: Attach IAM Role to EC2 Instances.
EBS Snapshots Explained
Amazon Elastic Block Store (or EBS for short) is a service for providing block storage to your EC2 instances. In other words, it provides reliable volumes (hard drives) to your cloud servers.
One very useful function of Amazon EBS is creating EBS snapshots of your EBS volumes. EBS snapshots are backups of your EBS volumes. But how do they work, and how can you use them? Let’s take a look.
Stop Limits When Stopping EC2 Instances
We have added a new option on our “Stop Multiple EC2 Instances” action that allows you to limit the number of EC2 instances that are stopped.
Instance Size Flexibility With Reserved Instances
Yesterday, AWS announced that their regional benefit EC2 reserved instances can be applied against any EC2 instance in the same EC2 instance family. We’ll explain to you exactly what that means.
Customize AMI Images
We have added some enhancements to two of our popular actions:
- Create AMI Image
- Create AMI Images
Now, you can customize properties of the volumes attached to the new EC2 instances created by the AMI image.
Archive Logs to Amazon S3
From its beginning, Skeddly has been logging all action activity in your Skeddly account. You can view any of these logs at any time within Skeddly, and you can download them individually, or in a monthly package. For many organizations, these logs are invaluable in their auditing strategies, much like CloudTrail is.
Starting today, we’re making it even easier for you to retain your own copy of your action logs. You can now archive your action logs to an Amazon S3 bucket in your AWS account.
Delete Unused WorkSpaces
At Eleven41 Software, we use AWS WorkSpaces for our all of our work. It allows us to connect to our working desktops from many different devices, and it helps keep our work secure from loss or theft.
However, it is possible for workspaces to get “forgotten”. This may happen for any number of reasons:
- A development workspace is no longer needed,
- An employee may have left the company
Leaving unused workspaces lying around will end up costing you money. Once a new month starts, each workspace will be charged it’s monthly price.
Today, we’re happy to announce a new action to help report on, and clean up, unused AWS WorkSpaces: Delete Unused WorkSpaces Workspaces.
Create Lightsail Instances From Snapshots
As we have previously discussed, Amazon Lightsail provides a simpler pricing model compared to Amazon EC2. However, you can still benefit from some cost-saving strategies with your Lightsail instances.
Like RDS and Redshift, you can schedule your Lightsail instances to be created each morning, and deleted each evening. This way, you won’t be charged for your instances overnight or over the weekend.
Today, we’re happy to announce a new Lightsail cost-savings action: Create Lightsail Instances From Snapshots.
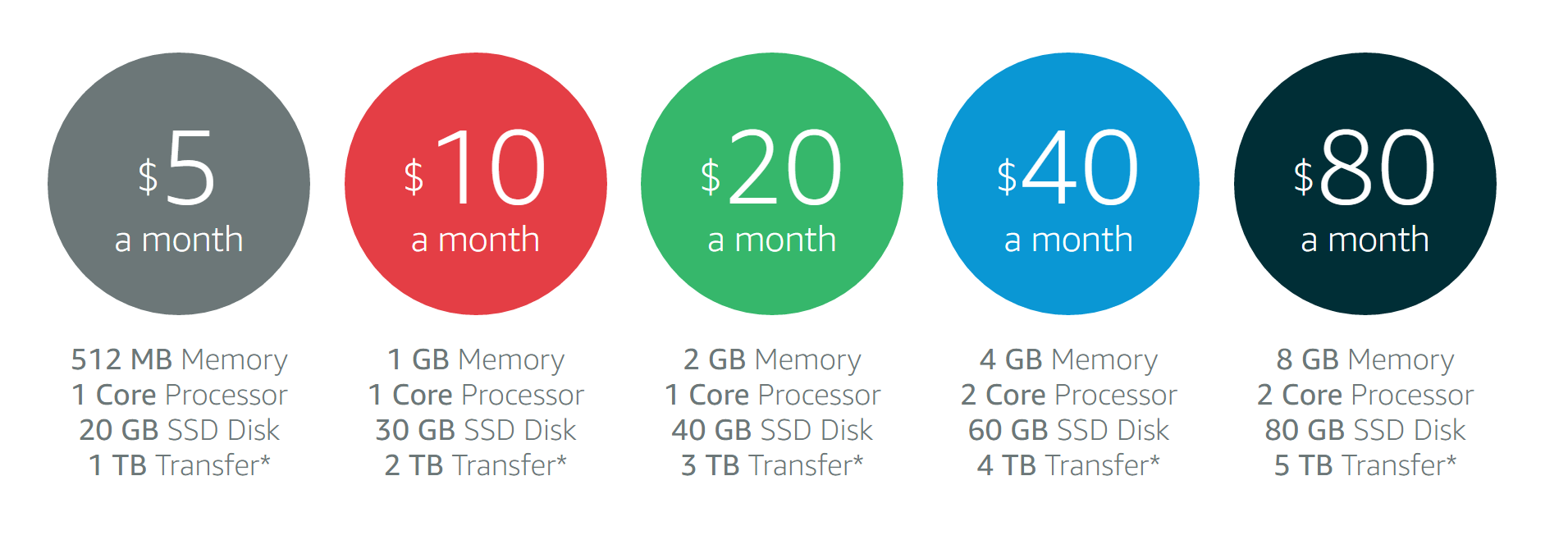
Understanding Lightsail Pricing
This article has been updated on 2017-01-27 to include some additional details regarding hourly prices and days-per-month differences.
Amazon Lightsail provides a simpler pricing model compared to Amazon EC2. The pricing for Lightsail is advertised “per month”. For example, $5 per month or $20 per month.
What isn’t up front is that, like EC2, you are actually charged for your Lightsail instances on an hourly basis. So, if your Lightsail instance only exists for 100 hours of the month, then you are only charged for those 100 hours.
Delete Lightsail Instance Snapshots
Earlier today, we announced our Create Lightsail Instance Snapshots action. Creating snapshots is a great practice, but you will also want to clean up old snapshots. This way, you won’t accumulate costs for unnecessary backups.
Today, we are also announcing the second of our Lightsail actions: Delete Lightsail Instance Snapshots.