Disable Unused IAM Access Keys Action
According to Best Practices for Managing AWS Access Keys, if you must utilize IAM access keys, it is best to remove or disable unused keys. This will close possible security holes in your AWS account.
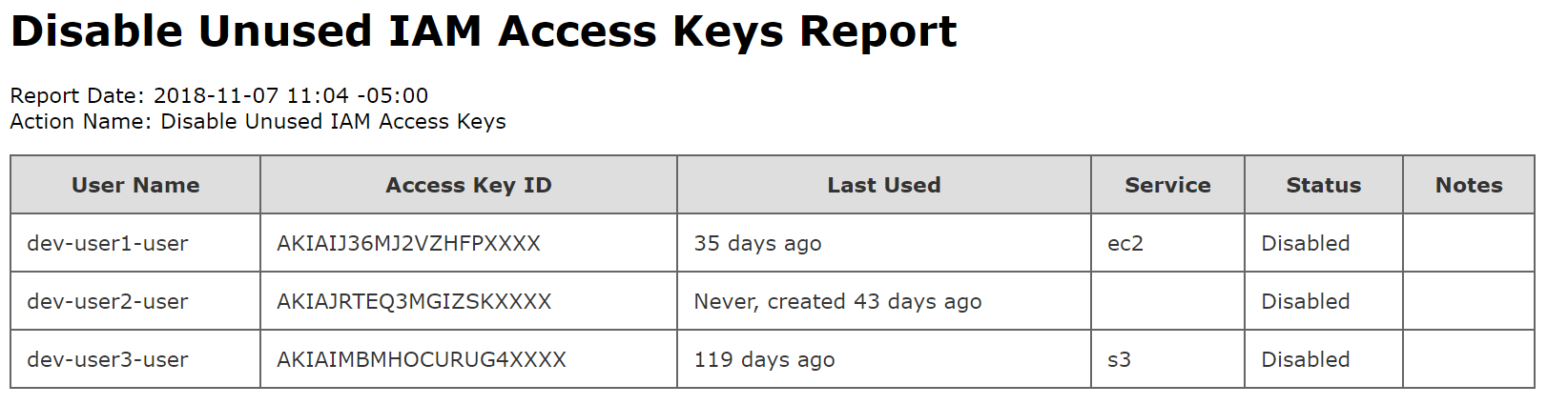
Today, we’re happy to announce a new action to help with this task: Disable Unused IAM Access Keys.
This new action will iterate through the IAM users in your AWS account, determine when any access keys were last used, and if they were not used inside a configurable threshold, disable the keys.
For example, you can disable any access key not used in the last 30 days.
The users that are affected by the action can be selected by:
- Checking all users
- Checking users matching a name comparison (eg. users that start with “dev-“)
When creating a new action, the default number of days to check for is 30 days. But this can be increased or decreased to meet your requirements.
Finally, when the action completes, an email can be sent reporting all the IAM user access keys that were disabled.
Full pricing information for this new action is available on our pricing page.
Try It Today
Keep your AWS account secure today. Sign-up for our 30 day free trial or sign-in to your Skeddly account to get started.